The Essential Guide to Microsoft's Conditional Access Recommendations
A consolidated, actionable guide to Microsoft Entra Conditional Access recommendations, with direct links to official documentation and policy guidance.
Microsoft’s Conditional Access documentation is extensive, but the specific recommendations are scattered across multiple articles and sections, making it difficult to get a consolidated view. This article compiles all of Microsoft’s explicit Conditional Access recommendations from official documentation into one structured, actionable reference. Each recommendation includes a direct link to the source material for further context and detail.
Design Guidelines
This section covers on design principles, operational resilience, policy rollout, and session management — as distinct from specific policy templates, which are covered in the next section.
Design principles
Source: Plan a Conditional Access deployment
- Use a structured naming standard that includes sequence numbers and has descriptive policy names.
- Ensure that every app has at least one policy applied.
- Minimize the number of policies by grouping users and apps covered by repetitive patterns.
- Use protected action as another layer of security on attempts to create, modify or delete policies.
- Implement policy assignments through groups, not individuals.1
- Ensure a consistent experience across Microsoft 365 client applications by implementing the same set of controls for services such as Exchange Online and SharePoint.1 2
To protect Conditional Access assignment groups, consider using role-assignable groups and/or placing them in restricted-management administrative units to prevent unauthorized modification.
Operational Resilience
Source: Create a resilient access control management strategy
- Provide multiple authentication methods for each user, using different communication channels.
- Combine multiple Conditional Access controls to avoid lockouts:
- Use Windows Hello for Business to satisfy MFA requirements at sign-in.
- Use trusted devices (hybrid-join or Intune-managed) to satisfy strong authentication requirements without implicit MFA challenge.
- Leverage risk-based policies that prevent access when the user or sign-in is at risk, in place of fixed MFA policies.
- Do regular reviews of the exception groups.1
- Deploy password hash sync even if federated or using pass-through auth.
- Maintain at least two cloud-only emergency permanent-admin accounts using *.onmicrosoft.com domain, phishing-resistant authentication (different to that of other admin accounts).3
- Implement disabled policies that act as secondary resilient access controls in outage or emergency access scenarios.4
- If using on-prem VPN with NPS extension, federate as a SAML app or plan how to disable or replace in an emergency.
Policy Deployment Process
Source: Plan a Conditional Access deployment
- Use Microsoft’s policy templates to get started with a secure baseline and expand from there.
- Evaluate impact with:
- Test thoroughly, report-only does not always match the actual behavior.
Consider using a phased rollout approach when deploying Conditional Access in production. There is no official guidance on this, but it can help reduce risk.
Session and Re-authentication Settings
Source: Reauthentication prompts and session lifetime
- Enable single sign-on across applications by using either:
- If reauthentication is needed, configure a sign-in frequency policy.
- For mobile users, encourage the use of the Microsoft Authenticator app to reduce authentication prompts.
- Avoid KMSI (Keep Me Signed In/Company Branding)- use Conditional Access to enforce persistent browser sessions instead.
Deprecation and Transition Guidance
- Migrate legacy risk policies from Entra ID Protection to Conditional Access.
- Legacy risk policies retire on October 1, 2026.
- Migrate to the Authentication Methods policy from Legacy MFA (per-user MFA) and SSPR policies.
- Legacy MFA/SSPR deprecation begins September 30, 2025.
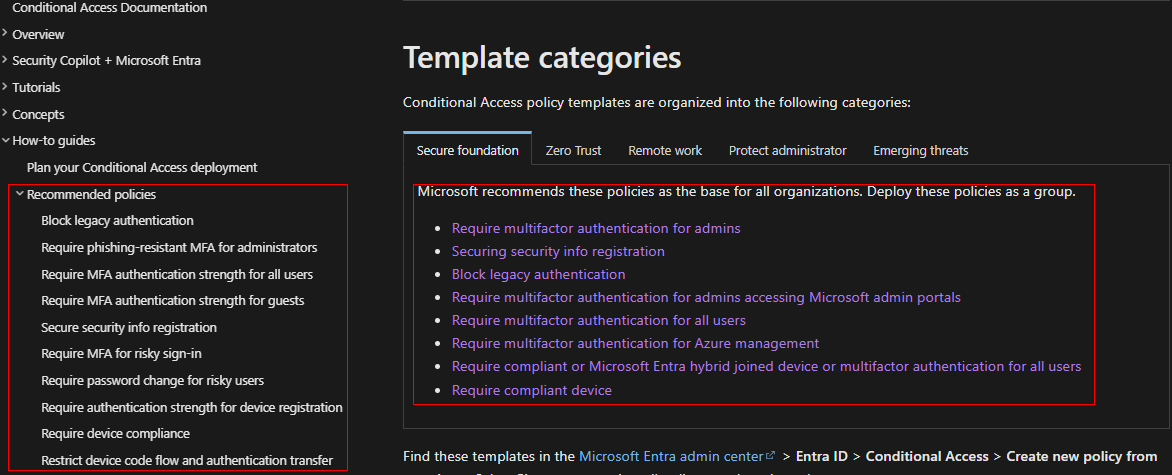
Recommended Policies
The ‘Secure foundation’ templates provide the minimum baseline that all organizations should implement first. These policies drive broad MFA adoption and device-based authentication, establishing essential security controls before advanced protections are implemented.
Once that baseline is in place, you can move toward more advanced protections. Focus on risk-based controls, phishing-resistant authentication for admins, authentication strength, and alignment with the Zero Trust model.
The recommended policies below support this progression. They introduce more granular and risk-aware access controls.
Secure foundation
- Block legacy authentication for all users
- Securing security info registration
- It’s recommended to use Temporary Access Pass (MFA) for registration of internal users.
- For guest users who need to register MFA in your directory, registration can be blocked outside a trusted network location.
- Require device compliance
Device compliance may be challenging to enforce in practice - see alternatives to device compliance below.
Zero Trust
- Require MFA authentication strength for all users
- Do not include any app exclusions for this policy, see ‘Conditional Access behavior when an all resources policy has an app exclusion’.
- Require MFA authentication strength for guests
- Require MFA for risky sign-in
- Require password change for risky users
- For passwordless accounts It’s recommended to BLOCK users at high risk.
Authentication strength is not supported for external users who authenticate with email OTP, SAML/WS-Fed or Google federation.
Emerging threats
Uncategorized
- Require authentication strength for device registration
- External authentication methods are currently incompatible with authentication strength (use MFA grant control instead)
- To enforce CA user action ‘Register or join devices’, ensure the corresponding MFA requirement in ‘Devices > Overview > Device Settings’ is disabled.
- Restrict device code flow and authentication transfer
- Block disallowed countries/regions (Recommended in ‘Plan your CA deployment’)
Alternatives to Device Compliance
- Require compliant or hybrid joined device for admins
- Require compliant, hybrid joined device OR MFA for all users
- Block unknown or unsupported device platforms
- Disable browser persistence
- Prevents persistent browser sessions from unmanaged devices.
Other Considerations
While the following topics are not explicitly listed as part of Microsoft’s conditional access recommendations, they represent practical and security-relevant scenarios that many organizations should consider:
- Conditional Access for workload identities to protect service principals.
- Conditional Access authentication context for PIM Role activation to ensure elevated access is subject to just-in-time controls.
- Reduce attack surface by monitoring and cleaning up inactive users, stale guests accounts and inactive workload identities.
- Use macOS Platform Single Sign-on to enable strong, seamless authentication on macOS- similar to how WHfB is used on Windows devices.
- Configure Single Sign-On for Linux to improve authentication on supported distributions.
- Prevent token replay attacks with Conditional Access Token Protection
License requirements
The table below summarizes license dependencies for features discussed in this article. Refer to the Microsoft Entra licensing for more details.
| License Tier | Required For |
|---|---|
| Microsoft Entra ID P1 | - Conditional Access |
| Microsoft Entra ID P2 | - Risk-based policies - Access Reviews (group membership) - Privileged Identity Management (PIM) |
| Entra ID Governance | - Access Reviews (Inactive Users) |
| Workload ID Premium | - Conditional Access for Workload IDs (service principals) |
What’s Next?
Conditional Access is evolving rapidly. These recommendations provide a solid foundation, but successful implementation requires structured policy design and consistent review.
For practical guidance, see Building Scalable Conditional Access – A Policy Framework for Zero Trust. It covers naming, layering, and organizing policies for complex environments.
Further reading
Microsoft:
- Common security policies for Microsoft 365 organizations (App protection and device compliance)
- Conditional Access optimization agent (“copilot” agent for CA)
- Protecting tokens in Microsoft Entra (harden devices and CA token protection)
- Conditional Access insights and reporting
- Developer guidance for Microsoft Entra Conditional Access
Other resource:
- Conditional Access Essentials: RMAUs, Named Locations, Authentication Strengths, Service Principals (excellent article with details on protecting groups)
References
1: Microsoft Entra authentication management operations reference guide 🔗
2: Service dependencies in Microsoft Entra Conditional Access 🔗
3: Manage emergency access accounts 🔗
4: Plan a Conditional Access deployment - Naming standards for emergency access controls 🔗
Changelog
- 2025-09-12: Updated the “What’s Next?” section to include a link to the CA Framework guide.
- 2025-09-04: Initial version.